New risks of WebAssembly (WASM): A Hidden Door for Malware?
Secure Web Gateways (SWGs) are increasingly vulnerable to 'Last Mile Reassembly Attacks' that leverage WebAssembly (WASM) to deliver malware directly to user browsers. These attacks bypass traditional SWG defenses, highlighting the need for browser-native security solutions to protect against modern web threats.
What is WebAssembly (WASM)?
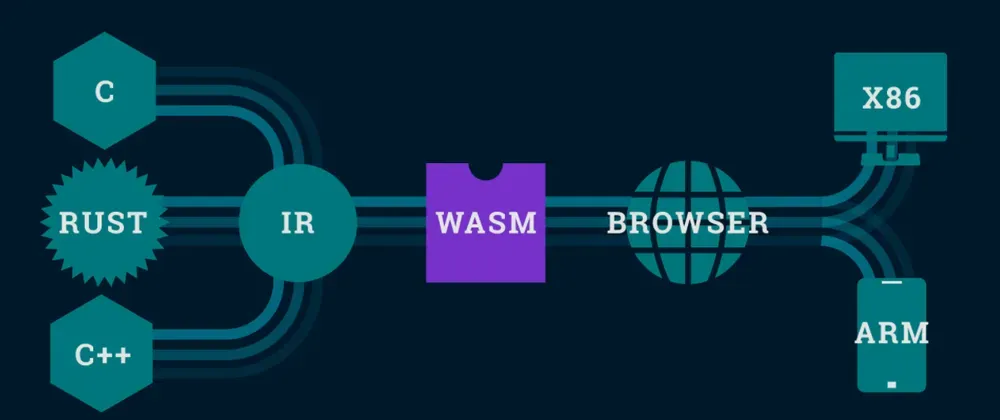
WebAssembly (WASM) is a binary instruction format that allows developers to compile code written in languages like C, C++, and Rust into a platform-agnostic, executable format that can be run in web browsers. This technology has revolutionized the way we build web applications, enabling faster execution, improved performance, and enhanced security. However, as we'll explore in this article, WASM's power can also be exploited by malicious actors.
What is a Secure Web Gateway (SWG)?
A Secure Web Gateway (SWG) is a cybersecurity product that protects company data and enforces security policies. SWGs operate between company employees and the Internet, filtering unsafe content from web traffic to stop cyber threats and data breaches. They also block risky or unauthorized user behavior. All SWG products contain essential technologies like URL filtering, anti-malware detection and blocking, and application control.
What is a Last Mile Reassembly Attack?
A Last Mile Reassembly Attack is a type of cyber attack that targets the final leg of a data transmission process, also known as the "last mile." This type of attack is particularly dangerous because it occurs when data is being transmitted from a secure network to its final destination, such as a user's device. During a Last Mile Reassembly Attack, a hacker intercepts and alters the data as it is being transmitted over the last mile, allowing them to gain access to sensitive information, such as login credentials or financial data.
The Rise of Last Mile Reassembly Attacks
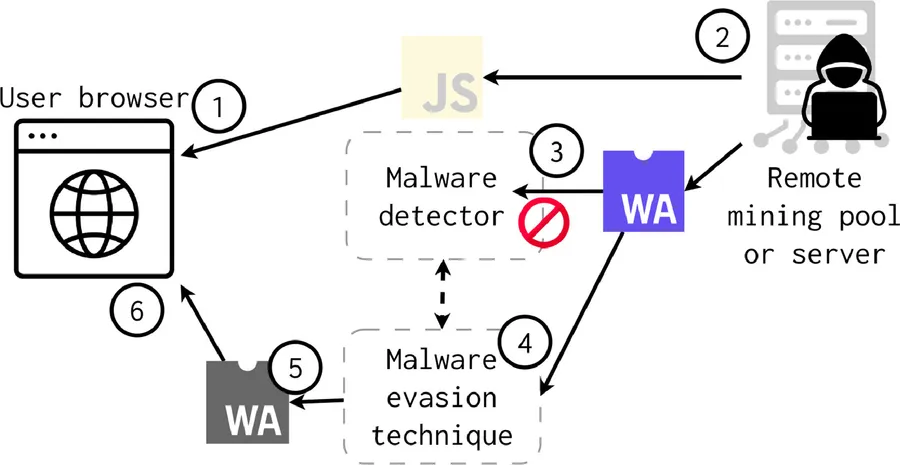
At DEF CON 32, SquareX Labs unveiled groundbreaking research exposing vulnerabilities in Secure Web Gateways (SWGs). These vulnerabilities allow attackers to execute 'Last Mile Reassembly Attacks,' bypassing traditional SWG defenses and delivering known malware directly to endpoints. This poses a significant threat to organizations that rely solely on SWGs for security.
WebAssembly: A Double-Edged Sword
One of the most concerning aspects of these attacks is the use of WebAssembly (WASM). While WASM offers numerous benefits, such as enhanced performance and efficiency in web applications, its power can also be exploited by malicious actors. Traditional SWGs primarily focus on inspecting network traffic at the HTML, CSS, and JavaScript layers, leaving them blind to the intricacies of WASM modules.
SWGs vs. WebAssembly: A Mismatch
The problem lies in the fact that SWGs lack the capability to perform dynamic analysis on WASM code. This means malicious payloads can be embedded within WASM modules and distributed through compromised or even legitimate websites, bypassing SWG detection mechanisms entirely. On the client-side, the malware is assembled and downloaded to the victim's endpoint.
The Need for Browser-Native Security
This vulnerability underscores the limitations of relying solely on network-layer defenses like SWGs in today's threat landscape. Enterprises need to adopt browser-native security solutions that operate directly within the browser, providing real-time analysis and control over WASM modules. These solutions offer a more effective approach to detecting and neutralizing threats before they can cause damage.
Protecting Your Organization
As WebAssembly continues to gain prominence in web development, organizations must recognize the evolving threat landscape and take proactive steps to protect their environments. This includes evaluating existing SWG capabilities and implementing browser-native security solutions designed to handle the complexities of modern web technologies.
Sources:

https://www.cloudflare.com/learning/access-management/what-is-a-secure-web-gateway/

Related content
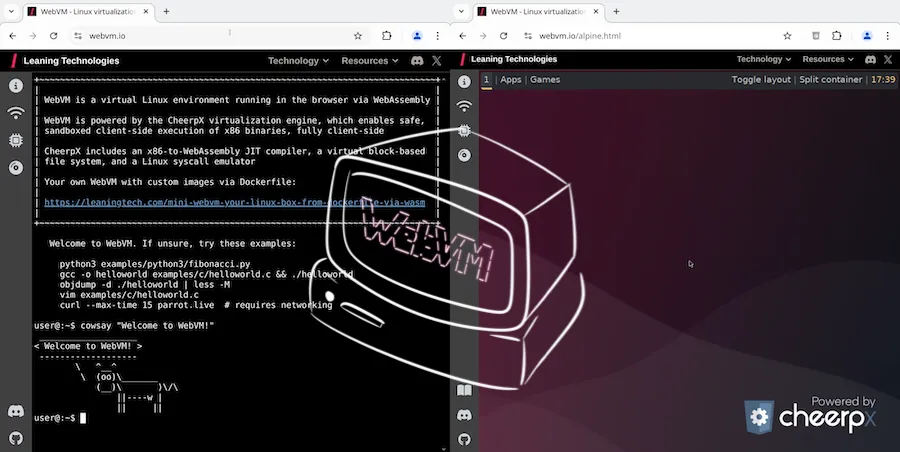
¿Cómo ejecutar un escritorio Linux en tu navegador? ¡WebVM 2.0 (WebAssembly) es la respuesta!
¡¿Espera, QUÉ?! ¿Recuerdas los días en que ejecutar un escritorio Linux completo significaba particionar discos duros, configurar gestores de arranque y sacrificar tu preciado fin de semana a los dioses de la administración de sistemas? Bueno, amigos, esos días se acabaron (más o menos). WebVM 2.0 te permite ejecutar
Read the full post →

How to run a Linux Desktop in your browser? WebVM 2.0 (WebAssembly) is the answer!
Wait, WHAT!? Remember the days when running a full Linux desktop meant partitioning hard drives, configuring bootloaders, and sacrificing your precious weekend to the gods of system administration? Well, friends, those days are over (sort of). WebVM 2.0 lets you run a complete Linux environment, including a desktop, entirely